Commview For Wifi Vs Wireshark
Wireshark - powerfull sniffer which can decode lots of protocols, lots of filters. Tshark - command line version of wireshark dumpcap (part of wireshark) - can only capture traffic and can be used by wireshark / tshark. Difference between sniffer tools. Wireshark/tshark /dumpcap can use tcpdump filter syntax as. Is it possible to capture packets between two devices in a wifi. Comparison of packet analyzers. CommView: TamoSoft: 6.5 GUI Proprietary. Wireshark (formerly Ethereal) The Wireshark team.
In this case, both products will be able to capture data simultaneously. If you start capturing with CommView first, WinPcap will fail to capture any packets for a reason unknown to us. When reconstructing TCP sessions that contain HTML pages in Japanese or Chinese, I can't see the original text. To see text in East Asian languages, you should install East Asian fonts. Open Control Panel => Regional and Language Options, select the 'Languages' tab, and check the 'Install files for East Asian languages' box. Can I save the audio from the VoIP analyzer to a standard.wav or.mp3 file? Not directly, but there are many utilities on the market that offer a 'virtual audio cable' that allows saving anything that is played back through your sound card to a file.
Contents • • • • General information [ ] Basic general information about the software—creator/company, license/price, etc. Creator Latest release User interface Cost Analyze This Web GUI N/A? Massimiliano Montoro 4.9.56 / April 7, 2014 GUI Freeware Free 11.1 / April 24, 2018 ( 2018-04-24) GUI $0-$995, depending on version??
Which tool (others not listed included) would you use to debug an interface? • wireshark - powerfull sniffer which can decode lots of protocols, lots of filters. • tshark - command line version of wireshark • dumpcap (part of wireshark) - can only capture traffic and can be used by wireshark / tshark • tcpdump - limited protocol decoding but available on most *NIX platforms • ettercap - used for injecting traffic not sniffing All tools use libpcap (on windows winpcap) for sniffing. Wireshark/tshark /dumpcap can use tcpdump filter syntax as capture filter. As tcpdump is available on most *NIX system I usually use tcpdump. Depending on the problem I sometimes use tcpdump to capture traffic and write it to a file, and then later use wireshark to analyze it. If available, I use tshark but if the problem gets more complicated I still like to write the data to a file and then use Wireshark for analysis.
Ok, I am connected to the LAN through a hub, but I can't see other machines' traffic again, as if it's a switch. Why is this so? There are two possible reasons: Either you have a hub that is only labeled as a hub, but inside is a switch (some vendors like Linksys do that), or you have a multi-speed hub, in which case you can't see the traffic from the stations operating at the speed that is different from your NIC's speed (e.g. If you have a 10 Mbit NIC, you can't see the traffic generated by 100 Mbit NICs). I have a home LAN connected to the Internet via a broadband router, and I can see only my own traffic. Is it possible to capture the traffic of other machines on my home LAN?
Overall, AirDefense Mobile’s packet-capture and analysis services are difficult to use and not competitive with the other products tested, marring an otherwise fine assurance tool. CACE Technologies AirPcap Ex, Wireshark and Pilot CACE is one of the most visible firms in network analysis, offering a number of products for wired and wireless applications. AirPcap consequently is one of the best-known tools for WLAN packet-capture and analysis (see screenshot above).
Can I save the audio from the VoIP analyzer to a standard.wav or.mp3 file? Not directly, but there are many utilities on the market that offer a 'virtual audio cable' that allows saving anything that is played back through your sound card to a file.
I am unsure what the following networking tools do. They all seem to do a similar thing. First some background. I am familiar with cisco IOS. I am doing some linux networking experimentation with virtual machines so I am trying to create a small virtual network.
So after step 7, it is advisable to leave the system alone for 2-3 hours and then proceed to the further steps! NOTE: Recently CommView became a paid software with a rather ridiculous price tag. But, no worries. There are more than enough alternatives.
You can disable this feature (Settings => Options => Disable DNS resolving), but in this case, the Latest IP Connections tab will not be able to show you the hostnames. Second, you may have configured the program to check if updates or new versions are available. To do this, CommView has to connect to. You can disable this feature (Settings => Options => Misc. => Enable automatic application updates). Third, when you purchase the product, you need to activate it. If you select online activation, CommView has to connect to.
Send to VoIP Analyzer – sends all packets from the current Log Viewer window to a new window for VoIP-specific analysis. Close Window – closes the window. Search Find Packet – shows a dialog that allows you to matching a specific text. Go to Packet Number - shows a dialog that allows you to jump to a packet with the specified number. Rules Apply – applies your current rule set to the packets displayed in Log Viewer.
Contents • • • • General information [ ] Basic general information about the software—creator/company, license/price, etc. Creator Latest release User interface Cost Analyze This Web GUI N/A? Massimiliano Montoro 4.9.56 / April 7, 2014 GUI Freeware Free 11.1 / April 24, 2018 ( 2018-04-24) GUI $0-$995, depending on version?? Karl van Randow 4.1.4 / July 10, 2017 GUI? $30-$50 (Free Trial) Clarified Analyzer GUI Non-free Clusterpoint Network Traffic Surveillance System web GUI?
Is there anything I can do about it? Yes, you can use the Open current buffer in new window button on the small toolbar on the Packets tab. This will allow you to make snapshots of the current buffer as many times as you wish, at any intervals.
In brief, yes. There are a few methods that can help you solve this problem.
There are two possible reasons: Either you have a hub that is only labeled as a hub, but inside is a switch (some vendors like Linksys do that), or you have a multi-speed hub, in which case you can't see the traffic from the stations operating at the speed that is different from your NIC's speed (e.g. If you have a 10 Mbit NIC, you can't see the traffic generated by 100 Mbit NICs). I have a home LAN connected to the Internet via a broadband router, and I can see only my own traffic. Is it possible to capture the traffic of other machines on my home LAN?
In such cases you do not need to guess the IP address available in the LAN segment, all you need to do is unbind the network adapter from TCP/IP and start capturing. Open Control Panel => Network Connections, right-click on the connection icon, select Properties, and uncheck the boxes corresponding to the protocols you don't want to be bound to the NIC. I'm on a LAN with high traffic volume, and it's hard to examine individual packets when the application is receiving hundreds of thousands of packets per second, as the old packets are quickly removed from the circular buffer. Is there anything I can do about it? Yes, you can use the Open current buffer in new window button on the small toolbar on the Packets tab. This will allow you to make snapshots of the current buffer as many times as you wish, at any intervals. You will then be able to explore the packets in these new windows at your leisure.
The value of capturing and analyzing network traffic is well established. After all, the generic “sniffer” has been a fixture of networking since the days of “datascopes” on RS-232 connections. Wireless links introduce a number of complicating elements to this process, however — Wi-Fi protocols are unique at Layer 2, and traffic over the air isn’t serialized, as is the case with wire. Simultaneous, competing traffic is often the norm. Packet-capture tools are no longer the first-line approach to troubleshooting, and many Wi-Fi assurance suites include a variety of capabilities that can resolve even vexing problems without resorting to protocol analysis. Nevertheless, there are times when an analysis of raw, real data is the only way to go, particularly when connection and authentication challenges are being diagnosed. Wi-Fi packet-capture and analysis products come in a number of forms.
And there is pretty good documentation and tutorial information on their website. Currports (and TCPView) outputs are quite different in both form and purpose (see fig 3 for a currports segment).
 I have also used Wireshark to do things like analyze potential problems in SSL/TLS handshaking for mail servers. Besides the timeline, you can select each line and get additional information on what is actually happening.
I have also used Wireshark to do things like analyze potential problems in SSL/TLS handshaking for mail servers. Besides the timeline, you can select each line and get additional information on what is actually happening.
Using Log Viewer is similar to using the Packets tab of the main window; please refer to the chapter if you need detailed information. Log Viewer Menu File Load CommView Logs – opens and loads one or several CommView capture files. Import Logs – allows you to import capture files created by other packet analyzers. Export Logs – allows you to export the displayed packets to capture files in several formats. Clear Window – clears the packet list. Generate Statistics – makes CommView generate statistics on the packets loaded in Log Viewer. Optionally, it is possible to reset previously collected statistical data displayed in the Statistics window.
Multi-language support. The new interface supports multiple languages. Wireshark ships with Chinese, French, German, Japanese, Polish and Italian as well as English, and more languages will be supported soon.
I can't see the traffic of other machines. Why is this so? Unlike hubs, switches prevent promiscuous sniffing. In a switched network environment, CommView (or any other packet analyzer) is limited to capturing broadcast and multicast packets and the traffic sent or received by the PC on which CommView is running.
Got all that? This process is much more difficult than it needs to be, and perhaps could be addressed quite simply by including instructions in the package. Our notebook configuration was used with the internal Intel adapter (and yes, we needed to know the model of the one installed) and AirMagnet’s C1060 802.11a/b/g/n PC Card. The OQO’s built-in Atheros Communications AR5006XS adapter was used for testing on that device. WiFi Analyzer has a huge range of functions, including security- and other vulnerability-monitoring, rogue detection, performance testing, inference-based interference analysis, and a detailed knowledge base called AirWISE. All this can make it a very good value for many organizations, because a broad range of features beyond packet-capture and analysis is desirable if not always required.
Installation was easy — just enter the serial number provided with the software license and select your adapter. Our internal WLAN adapter was not supported by OmniPeek, so we used a Linksys WUSB600N dual-band 802.11n adapter with the required custom driver provided by WildPackets. We did not use the OmniEngine component, a Windows service that is designed for larger, distributed (including multi-site) monitoring and capture applications.
The PC version’s features were identical to the Micro PC version, but the convenience of the latter was undeniable — the OQO is a bit larger than a typical PDA-form-factor handset, but is a full-function Windows XP machine. This form factor is quite appropriate to Wi-Fi troubleshooting and analysis activities, which can require a high degree of mobility. Some might have a problem with eyestrain because of OQO’s smaller screen, but this issue is partially remedied by the handy screen-magnifier buttons on its keyboard. Installing WiFi Analyzer is complex because of licensing issues, as is often the case. There are a license number and a “serial key” to enter, but don’t enter them on the device — instead, include this step as part of the registration process on the AirMagnet support page.
I am unsure what the following networking tools do. They all seem to do a similar thing. First some background. I am familiar with cisco IOS. I am doing some linux networking experimentation with virtual machines so I am trying to create a small virtual network.
I'm often logged on as a user without administrative privileges. Do I have to log off and then re-logon as the administrator to be able to run CommView? No, you can open CommView folder, right-click on the CV.exe file while holding down the Shift key, and select 'Run As' from the pop-up menu. Enter the administrative login and password in the window that pops up and click OK to run the program. Under Windows Vista and higher, CommView is automatically launched with elevated rights. Can CommView monitor a network adapter when running under Microsoft Virtual PC?
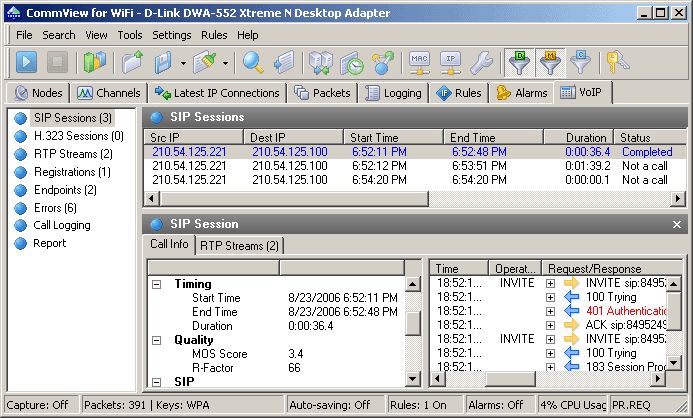
Viewing Logs Log Viewer is a tool for viewing and exploring capture files created by CommView and several other packet analyzers. It has the functionality of the Packets tab of the main program window, but unlike the Packets tab, Log Viewer displays packets loaded from the files on the disk rather than the packets captured in real time.
You can avoid this by selecting manual activation. These are the only types of connections CommView can potentially make. There are no other hidden activities. We don't sell spyware.
Close Window – closes the window. Search Find Packet – shows a dialog that allows you to matching a specific text. Go to Packet Number - shows a dialog that allows you to jump to a packet with the specified number.
Log Viewer can be used for exploring capture files created by other packet analyzers and personal firewalls. The current version can import files in the Network Instruments Observer®, Network General Sniffer® for DOS/Windows, Microsoft® NetMon, WildPackets EtherPeek™ and AiroPeek™, Wireshark/Tcpdump, and Wireshark/pcapng formats. These formats are also used by a number of 3rd-party applications.
Karl van Randow 4.1.4 / July 10, 2017 GUI? $30-$50 (Free Trial) Clarified Analyzer GUI Non-free Clusterpoint Network Traffic Surveillance System web GUI?
Viewing Logs Log Viewer is a tool for viewing and exploring capture files created by CommView and several other packet analyzers. It has the functionality of the Packets tab of the main program window, but unlike the Packets tab, Log Viewer displays packets loaded from the files on the disk rather than the packets captured in real time. To open Log Viewer, click File => Log Viewer in the program's main menu, or just double-click on any CommView capture file that you have previously saved. You can open as many Log Viewer windows as you wish, and each of them can be used for exploring one or several capture files. Log Viewer can be used for exploring capture files created by other packet analyzers and personal firewalls. The current version can import files in the Network Instruments Observer®, Network General Sniffer® for DOS/Windows, Microsoft® NetMon, WildPackets EtherPeek™ and AiroPeek™, Wireshark/Tcpdump, and Wireshark/pcapng formats.
I am connected to the LAN through a switch, and when I launch CommView, it captures only the packets sent to and from my machine. I can't see the traffic of other machines. Why is this so?
I am familiar with cisco IOS. I am doing some linux networking experimentation with virtual machines so I am trying to create a small virtual network. I started playing with virtual interfaces (tun/tap, loop br etc) and I'd like to be able to examine the traffic going through them for debug purposes. I'm a bit unsure of what tool to use. I know of the following: • tshark (wireshark) • dumpcap • tcpdump • ettercap I think tshark/wireshark uses dumpcap underneath.
In fact, the network adapter does not need to be bound to TCP/IP or any other protocol. In a situation where you are troubleshooting a network it might be necessary to be able to plug in the computer running CommView into an available port on a hub. In such cases you do not need to guess the IP address available in the LAN segment, all you need to do is unbind the network adapter from TCP/IP and start capturing. Open Control Panel => Network Connections, right-click on the connection icon, select Properties, and uncheck the boxes corresponding to the protocols you don't want to be bound to the NIC.
Besides the timeline, you can select each line and get additional information on what is actually happening. And there is pretty good documentation and tutorial information on their website. Currports (and TCPView) outputs are quite different in both form and purpose (see fig 3 for a currports segment).
With respect to packet-capture and analysis, however, the suite serves primarily as a source from which to get the custom drivers required to turn a set of otherwise ordinary Wi-Fi cards into sensors and (for our purposes here) packet-capture vehicles. The Aruba suite then fires up Paglo Labs’ Packetyzer 5.0.0 analysis tool, which, when enabled by the customized Aruba drivers, does a serviceable job of capturing and analyzing 802.11 frames. Packetyzer was developed originally by Network Chemistry, and the current release dates back to 2006. Not otherwise capable of 802.11 packet-capture and analysis, Packetyzer depends on RFprotect Mobile only as a source of drivers — it might be a good tool on its own if Aruba should decide to make the drivers available separately. Packetyzer is free, based on Ethereal, and it’s also open source. Download aplikasi whatsapp untuk hp nokia 501. Packetyzer’s age shows a bit; it’s not very visually appealing, and the help file is incomplete. But there are a lot of functions if one is willing to explore, including statistical analysis of captured data and very robust filtering capabilities.
Such automatic logging will make the application dump all the captured packets to file(s) continuously, and you can set any limit on the total size of the captured data. My network connection is via a cable/xDSL modem. Will CommView be able to monitor traffic on it?
Sorry, PPP handshaking packets cannot be captured. Note that all other PPP packets that follow the initial handshaking process are captured. I use WireShark and I noticed that it could no longer capture packets after CommView had been installed. There is a known conflict between WinPcap, the driver used in WireShark and many similar products, and the driver used in CommView. There is a simple workaround: Start capturing packets with WireShark before you start capturing packets with CommView. In this case, both products will be able to capture data simultaneously.
Comm View
It’s based on the very popular, open source Wireshark (formerly Ethereal) protocol analyzer. AirPcap adds the wireless-specific parts, and includes a Wi-Fi receiver as part of the package — no other adapter is required, so getting up and running is quick and easy: install the driver (as is always good practice, don’t use the included CD — download the latest version), insert the USB adapter, install Wireshark — and that’s it.
Wireshark/tshark /dumpcap can use tcpdump filter syntax as capture filter. As tcpdump is available on most *NIX system I usually use tcpdump.
Commview For Wifi 7.1
Improved statistics dialogues. In the Statistics and Telephony menus, the backend code has been consolidated so that most of Wireshark's statistics now share common internal logic. This should allow workflow improvements and a much more consistent interface, according to the developers. For more information about Wireshark and how to use it, see the Paul Rubens has been covering enterprise technology for over 20 years. In that time he has written for leading UK and international publications including The Economist, The Times, Financial Times, the BBC, Computing and ServerWatch.